
Our MSSP solution is based on LevelBlue USM Anywhere, a SaaS security monitoring platform that centralizes threat detection, incident response, and compliance management across on‑premises, cloud, and hybrid environments.
LevelBlue’s USM Anywhere is a platform that combines Asset Discovery, Intrusion Detection, SIEM and Log Management, Vulnerability Management, Behavioral Analysis, compliance reporting and more into one platform. LevelBlue is the only platform that integrates all these features under one pane of glass.
LevelBlue features can best be defined through its five major security functions that provide enhanced visibility to your IT operating environment. These functions allow LevelBlue USM to deliver threat detection, incident response, and compliance management across all IT environments. The security functions are:
SIEM
- Log Management that ingests and analyzes logs from different systems including Windows, Linux, etc.
- Open Threat Exchange (OTX) allows LevelBlue USM to quickly identify if an endpoint has been compromised and provides over 19 million threat indicators daily from over 100,000 global contributors that investigate emerging threats.
- Event Correlation that puts together all the events in your IT environment and raises an alarm if an incident is identified.
- Incident response that can be used as is or integrated into your existing incident response process.
- Data is encrypted in transit using TLS 1.2 and at rest using AES‑256 (for both hot and cold storage).
- Raw logs are retained in cold storage for the life of the active subscription. If the subscription is not renewed, data is retained for a short grace period and then destroyed.
Asset Discovery
- Performs an active and passive scan of the network to identify all IT assets with an IP address in the network(s).
- Maintains an inventory of all identified assets.
- Maintains an inventory of all identified software, mapped to the assets.
Vulnerability Scanning
- Provides continuous vulnerability monitoring that can be scheduled to suit your environment.
- Allows for authenticated and unauthenticated scans of the IT assets.
- Identifies risks and remediations based on industry standards scheme.
- Uses the identified risks in analysis and correlation.
Intrusion Detection
- Network IDS (NIDS) identifies threats in the network by analyzing network traffic.
- Host IDS (HIDS) identifies threats that may exist and/or affect an endpoint.
- File integrity monitoring allows LevelBlue USM to monitor changes to identified files and folders.
Behavior Analysis
- NetFlow analysis that identifies insecure protocols and services as well as source and destination IP addresses to perform forensic assessments, etc.
- Provides and monitors service availability.
A summarized features of USM Anywhere’s capability is shown in the diagram below:
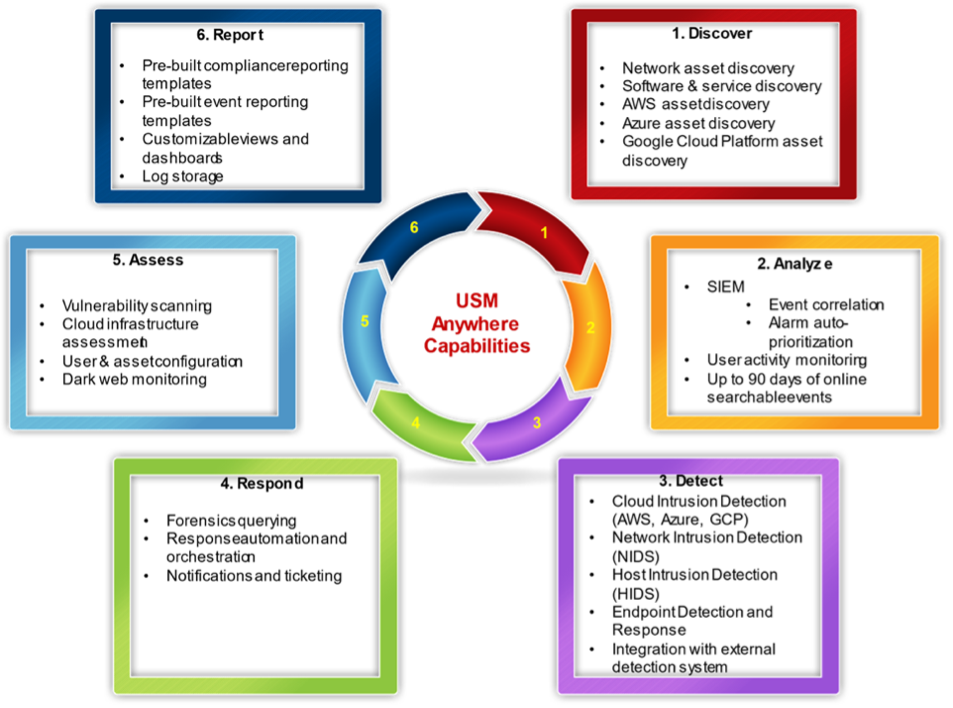
SM can also integrate with Microsoft Defender XDR (Defender for Endpoint, Defender for Office 365, Defender for Identity, Defender for Cloud Apps) by ingesting alerts and logs into our SOC platform. Although the above references USM Anywhere by default, our engineering team can incorporate Microsoft’s extended detection telemetry, ensuring continuous protection across your endpoints and cloud services.
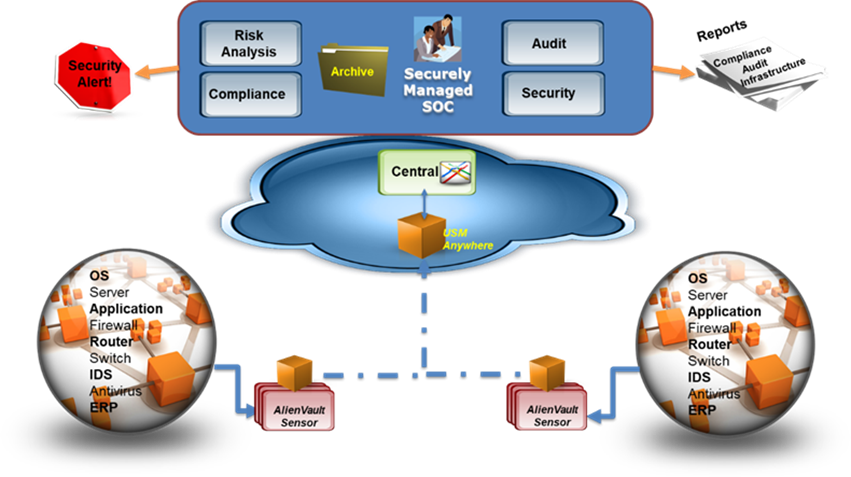
LevelBlue USM supports tiered and distributed architecture. At the bottom of this architecture are the agents that are installed on the endpoints. The agent can be LevelBlue’s native agent or NxLog service, if NxLog is already installed. Where the system supports syslog, the syslog can be forwarded to LevelBlue so that the USM Anywhere serves as the syslog server. As such system log events from Windows, Linux, and network infrastructure are ingested and analyzed by USM Anywhere.
Depending on the size of the organization, one or more sensors are deployed within the organization. The sensor is responsible for performing the grunt work of discovering assets, performing vulnerability scans, identifying software, etc. The LevelBlue sensor can be installed on a VMware, Hyper-V, Azure, or AWS platform.
As the sensors collect events, these are forwarded to the sub-domain in the cloud for analysis and correlation. In case of a security incident, an alarm will be generated at the sub-domain. The browser portal provides access to the users at the sub-domain where the users can view alarms, configure the system, or generate reports. What the user can do depends on the access rights granted to the user.
LevelBlue Features: BlueApp, Advanced BlueApp and Plugins
LevelBlue provides a seamless integration to a list of cloud applications through its BlueApps integration. Some examples of these integrations include Microsoft 365, Defender, Microsoft Azure subscriptions, CrowdStrike, SentinelOne, Windows and Linux Servers, Cisco, FortiGate, Palo Alto, Amazon AWS, Google GSuite, McAfee ePO, ProofPoint, Sophos, Carbon Black, SolarWinds, Active Directory, Barracuda Email Security Gateway, VMware, Veeam, Exchange 2016 etc. The list of applications continues to grow.
With BlueApps, our clients can monitor more of their security posture directly within the USM platform. BlueApps also enables clients to automate and orchestrate response actions when threats are detected, greatly simplifying and accelerating the threat detection and incident response processes.
Through use of BlueApps, our clients can:
- Centralize all the log data within USM Anywhere
- Respond to threats faster
- Data enrichment to perform analytics faster and more accurately
- Orchestrate and automate
Advanced BlueApps
In addition to the standard BlueApps functionality, Advanced BlueApps offer even more robust automation and orchestration capabilities. Advanced BlueApps collect and enrich log data, perform threat analysis, and provide workflow that coordinates response actions with third-party applications to provide security orchestration, allowing your IT team to take immediate action directly from the USM platform.
Plugins
In addition to the BlueApps ecosystem, USM Anywhere includes hundreds of plugins, so you can readily ingest security data from the existing data sources in your environment. The USM Anywhere plugin library provides source-optimized data collection for a complete range of technologies, making it easy for you to get complete visibility into your entire environment. These plugins may also be APIs that can connect using REST API infrastructure.
In those unique situations where there is no BlueApp or Plugin available to ingest the logs into USM Anywhere, Securely Managed will work with LevelBlue to build a plugin for most commercially available products at no additional charge.
In those unique situations where there is no AlienApp or Plugin available to ingest the logs into USM Anywhere, Securely Managed will work with LevelBlue to build a plugin for the most commercially available products at no additional charge.
LevelBlue Features: Log Types, Sources, Capacity and Retention
The following log types and sources can be ingested into USM Anywhere:
- Syslog: Many devices and operating systems support the syslog protocol, allowing logs to be sent directly to the USM Anywhere Sensor.
- Scheduled Log Collection Jobs: USM Anywhere can retrieve logs from specific locations through scheduled jobs.
- LevelBlue Agents: Registered LevelBlue Agents communicate securely to send data directly to USM Anywhere.
- BlueApp Integrations: You can configure integrations with third-party applications to collect logs.
- Azure Logs: If you stream data to Azure Event Hubs, you can connect an Azure Sensor to your event hub and collect:
- Azure Active Directory (AD) logs, including audit logs and sign-in logs.
- Azure Monitor logs.
- Azure SQL Database logs.
- Microsoft Defender Advanced Threat Protection (ATP) logs.
- AWS Logs: USM Anywhere can collect logs from AWS resources, including:
- AWS CloudTrail Logs
- Amazon S3 Access Logs
- ELB Access Logs
- Amazon Virtual Private Cloud (VPC) flow logs
- Raw Logs: USM Anywhere archives raw event data as logs, which are valuable for forensic analysis and compliance.
- Linux Logs: You can capture Linux logs using tools like NxLog and forward them to LevelBlue.
- Capacity: USM Anywhere can support small, medium, large and mega companies with their log-ingestion requirements. USM Anywhere scales from 125GB per month of storage to over 100TB of storage per month. This storage capacity allows organizations to scale up or down on event ingestion requirements and meet the requirements of Events Per Second (EPS).
- Retention: USM Anywhere retains the logs for as long as the licensing agreement is active in cold storage. The logs are available for retrieval at any time. In addition, the logs are maintained in hot storage from 15 days to 180 days based on your license.
LevelBlue Features: LevelBlue Labs and Open Threat Exchange (OTX)
With unrivaled visibility of LevelBlue’s IP backbone, global USM sensor network, and the Open Threat Exchange (OTX), LevelBlue Labs delivers continuous, tactical threat intelligence to the USM platform to keep your defense up to date.
Threat sharing in the security industry remains mainly ad-hoc and informal, filled with blind spots, frustration, and pitfalls. LevelBlue’s vision is for companies and government agencies to gather and share relevant, timely, and accurate information about new or ongoing cyberattacks and threats as quickly as possible to avoid major breaches (or minimize the damage from an attack).
The LevelBlue Labs® Open Threat Exchange® (OTX™) delivers the first truly open threat intelligence community that makes this vision a reality.
OTX provides open access to a global community of threat researchers and security professionals. It now has more than 100,000 participants in 140 countries, who contribute over 19 million threat indicators daily. It delivers community-generated threat data, enables collaborative research, and automates the process of updating security infrastructure with threat data from any source. OTX enables anyone in the security community to actively discuss, research, validate, and share the latest threat data, trends, and techniques, strengthening your defenses while helping others do the same.
LevelBlue Labs and OTX detectors is aligned with indictors from MITRE ATT&CK framework.
The diagram below reflects the resilient threat detection enabled through LevelBlue Labs and OTX and its lifecycle: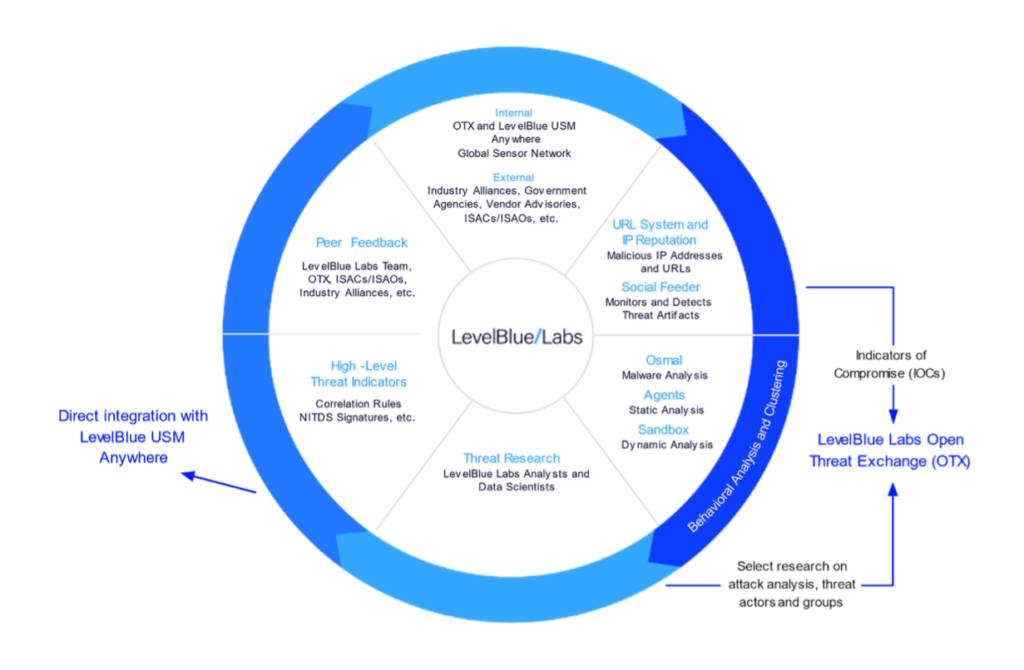
The benefits of LevelBlue Labs and OTX to our clients are several, including but not limited to:
- Timely and tactical cyber threat intelligence
- Delivering deep insights into adversaries and attacks
- And more importantly, automating proactive threat hunting (LevelBlue writes and updates the USM Anywhere correlation rules and threat indicators needed to continuously detect and prevent attacks)
The diagram below shows the integration of intelligence gathered by LevelBlue Labs and OTX with USM Anywhere (for entire IT environment – on premise and in the cloud):
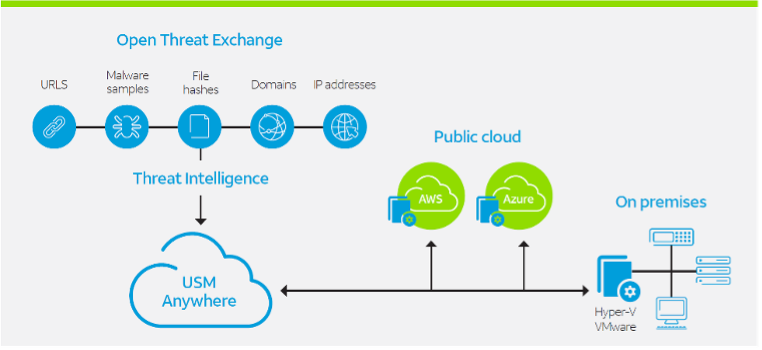
The diagram below reflects the continuous updates to USM Anywhere through intelligence gathered from Alien Labs and OTX:
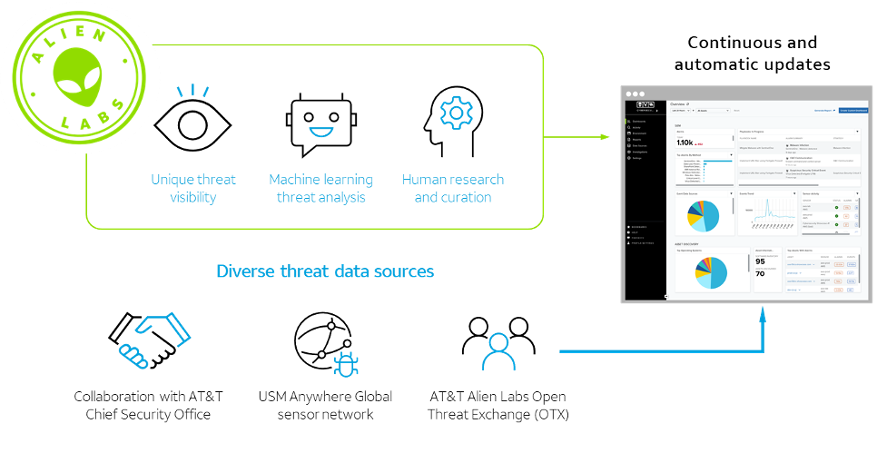 LevelBlue Features: Security Orchestration, Automation and Response
LevelBlue Features: Security Orchestration, Automation and Response
Through the use of Advanced BlueApps, Security Orchestration, Automation and Response (SOAR) is achieved to automate the workflow and respond to the alarms generated by LevelBlue. The following table shows a sample of products with Advanced BlueApps.
Securely Managed can review a complete list of Advanced BlueApps and map the District’s software licenses to Advanced BlueApps.
The District can save time, money and resources with this integration and orchestration. Some examples where Securely Managed has deployed SOAR capabilities are listed below:
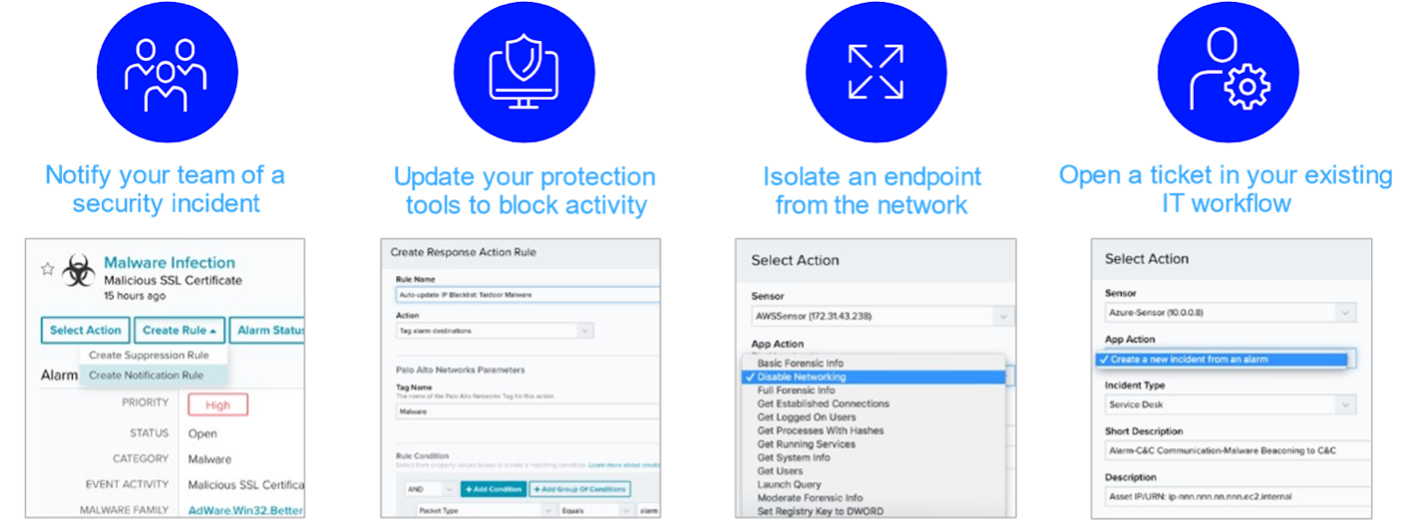
LevelBlue Features: Investigation and Case Management
The investigation feature of LevelBlue provides clients the ability to:
- Create New Investigation
- Edit Investigations
- View Investigations Details
- Activity on Investigations
- Notes on Investigations
- Evidence on Investigations
- Delete Investigations
- Notification Rule for Investigations
A screen shot of LevelBlue investigation screen is shown below:
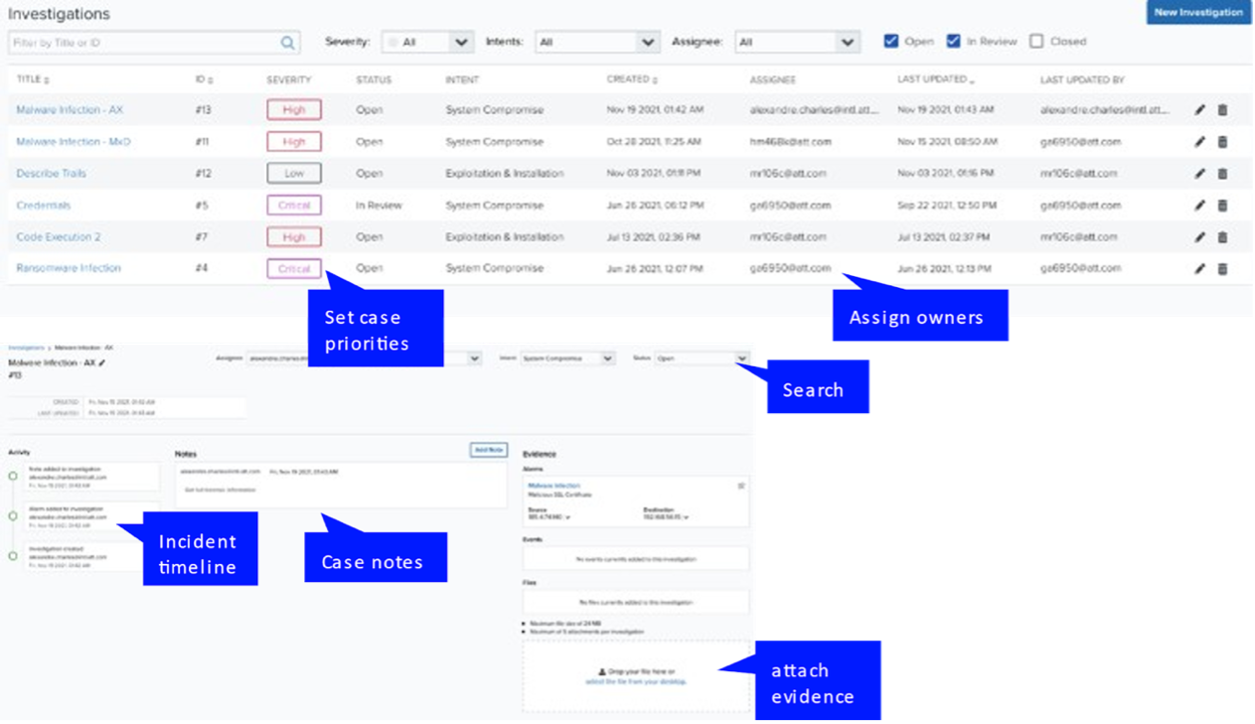
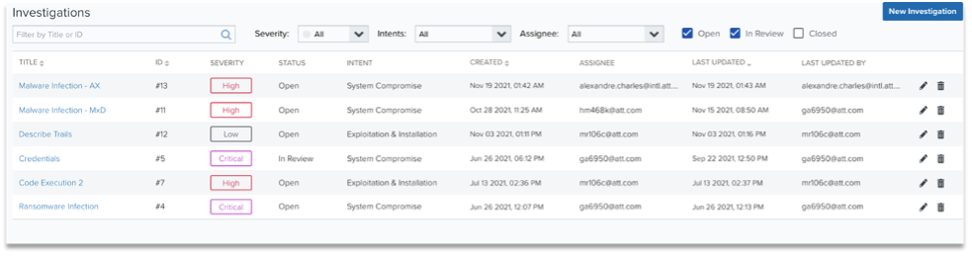
LevelBlue Features: Compliant with Industry Frameworks
LevelBlue has made compliance a top priority for clients and for themselves. LevelBlue has adopted the NIST Cybersecurity Framework (CSF), aligning their security controls and processes with industry-proven security best practices. LevelBlue uses their own USM platform to demonstrate and maintain compliance, working with third-party auditors to regularly test their systems, controls, and processes.
Their current compliance comprises of:
- Aligned with NIST Cybersecurity Framework (NIST CSF)
- PCI DSS Level 1 Service Provider
- ISO 27001:2013 Certified Compliant
- SOC 2 Type 2 Certified Compliant
- Support HIPAA Regulatory Compliance
- Certified Azure & AWS Advanced Technology Partner
- Third-Party Verified as GDPR Ready
- Utilizes FedRAMP Moderate Authorization
LevelBlue Features: Reporting
The LevelBlue USM Anywhere overview dashboard shown below provides various types of information immediately to the user. In addition to the overview dashboard, LevelBlue USM has other information and configuration screens that provide more detailed information through its drill-down capability. In addition, it provides search and filtering capabilities to allow the user to reduce the scope of displayed items.
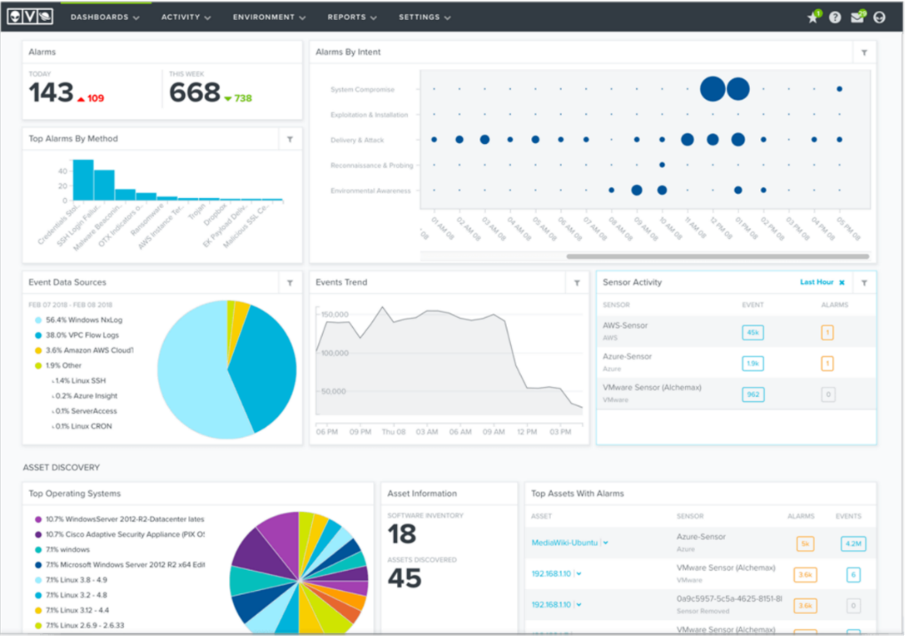
Overview Dashboard
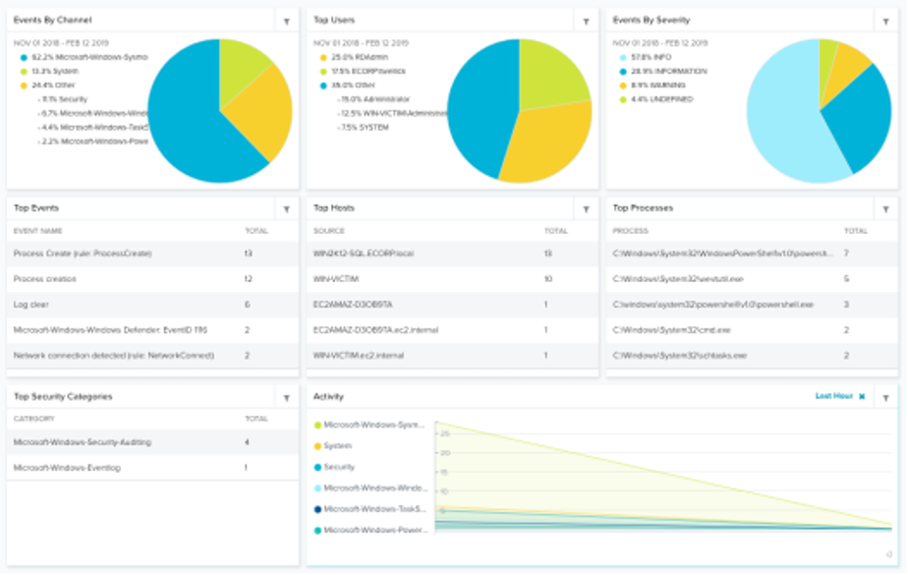
Windows Assets Dashboard
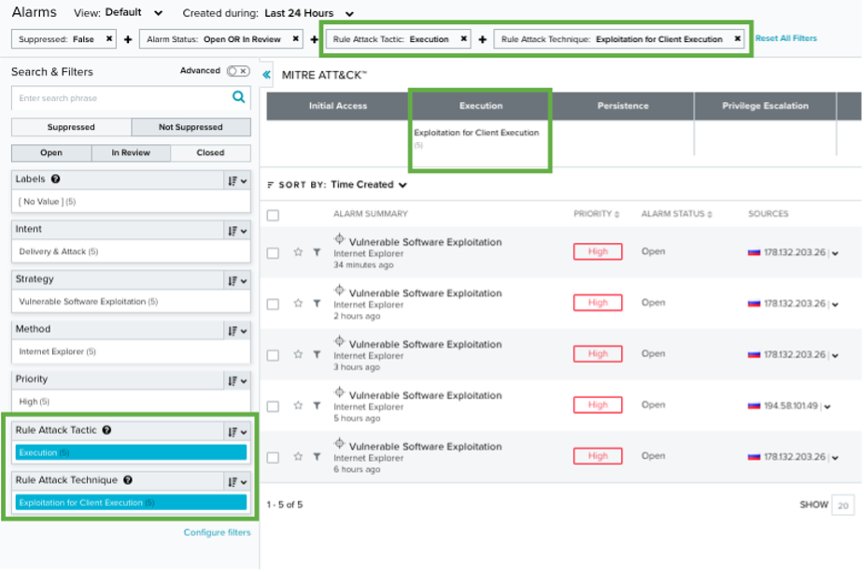
Alarms List
LevelBlue has a plethora of out-of-the-box reports and customizable reports available through their dashboard. The data on the dashboards are real-time and have the latest information. Our SOC also provides customized reports with additional trend data:
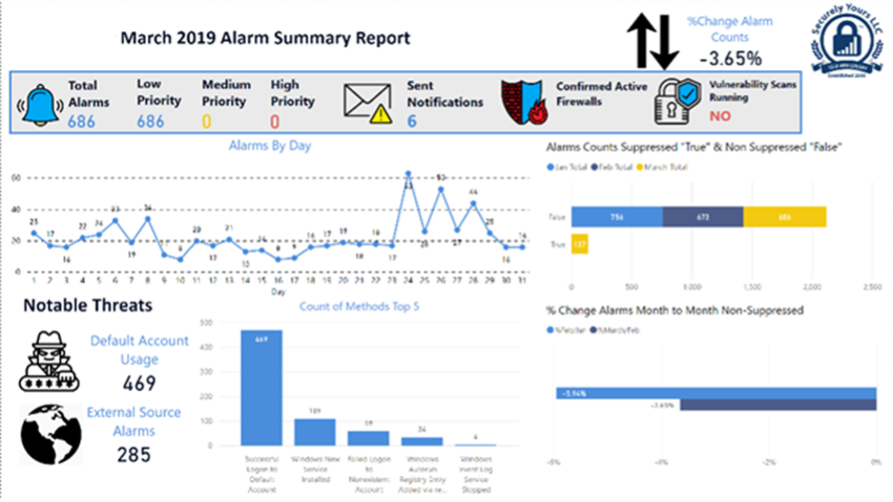
Executive Report – Generated by SM SOC
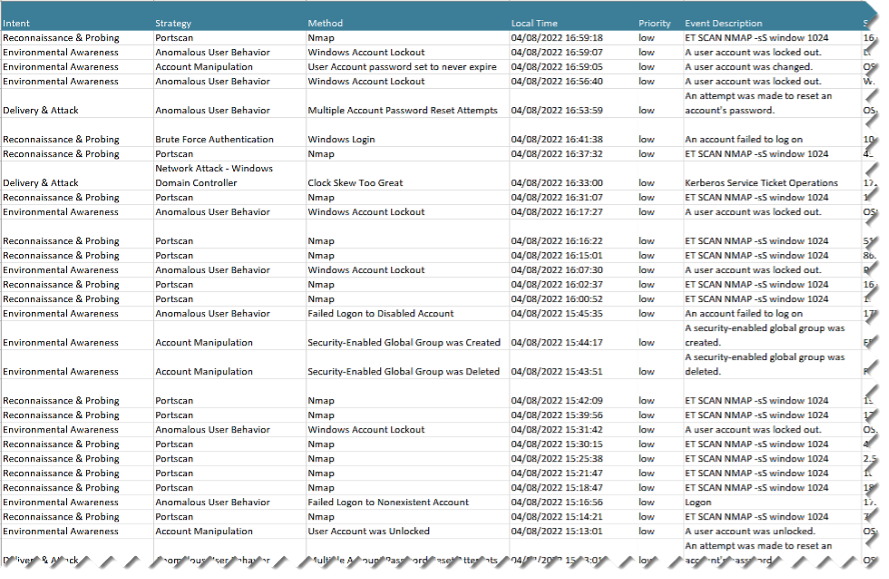
Sample Low Alarms List
LevelBlue Features: USM Anywhere as XDR
The detection and response industry is continuously evolving, and the current trend is to have a holistic view of threats across endpoints, servers, cloud environments and network, while applying analytics and automation to advanced threats that are detected. This in essence is the definition of Extended Detection and Response or XDR. It is accomplished through the feeds provided by the Endpoint Detection and Response (EDR) – which is focused on threat and detection/response on endpoints and Network & Cloud Detection & Response (NDR) – which is focused on detecting threats in network traffic flows and cloud-specific data. This relationship is shown in the diagram below:
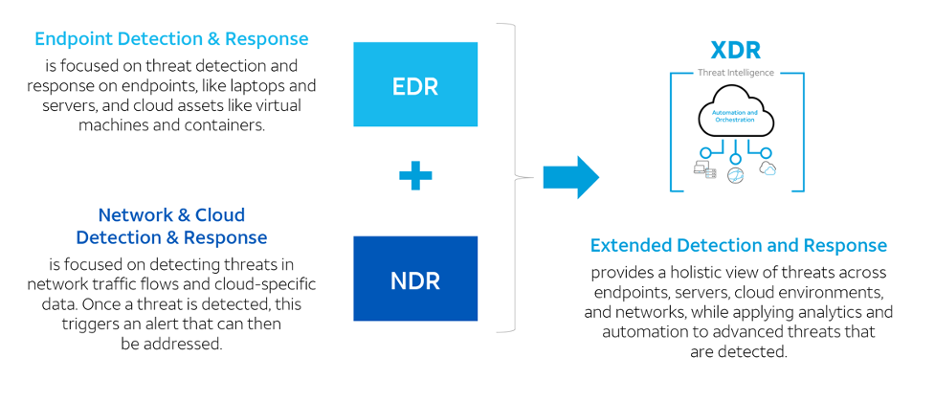
LevelBlue plays the role of the XDR by integrating the feeds from EDR and NDR and provides the continuous monitoring through single pane of glass.
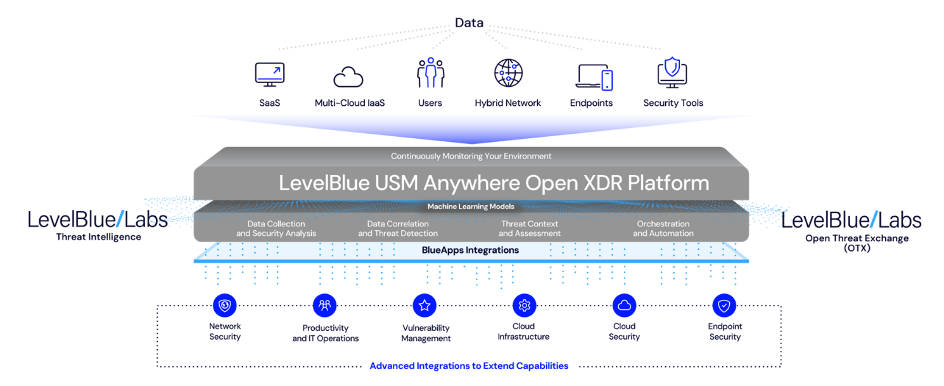 Securely Managed SOC Services
Securely Managed SOC Services
Securely Managed (SM) has been operating 24x7x365 virtual Security Operations Center (SOC) since 2017. The entire SOC infrastructure and personnel is based in United States and no client information ever leaves United States. SM resources work exclusively for SM and no portion of the service is outsourced to sub-contractors and 3rd party vendors (besides the licensing of AlienVault USM Anywhere through LevelBlue).
SOC Services
SM’s SOC by default includes but is not limited to the following services:
- 24×7 monitoring with a human capable of neutralizing threats immediately
- Log aggregation, automated parsing, coupled with human eyes on a SIEM
- Create operational playbook (run books) and escalation procedures
- Notification of alarms within the agreed upon Service Level Agreements (SLAs), usually within 15 minutes
- Daily (within 24 hours) and Monthly (within 30 days) reporting
- Monthly meetings with the client
- Custom configuration of AlienVault
- Custom rules
- Modification of current rules
- Monitoring the usage of storage
- Assist in ingesting log of new technologies deployed by the client
- Ensuring the critical assets are ingesting logs
- Monitoring the sensors and the connection to USM Anywhere
- Training for client personnel on use of USM Anywhere, custom reporting and SOC services
Incident Response Services
In terms of data breach risk assessment, SM SOC provides the following services:
- Develops and implements use cases and a playbook for Agency
- Conducts periodic assessments based on the use cases
- Conducts threat hunting
- Updates use cases and playbook from information gleaned from periodic MITRE ATT&CK and other proactive threat hunting procedures
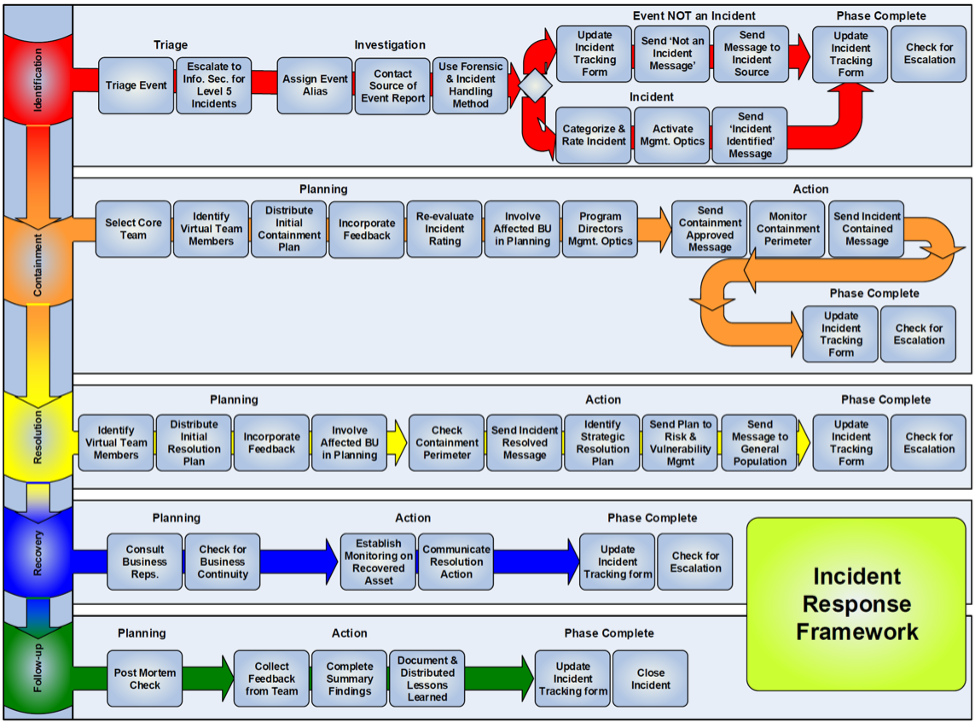
- Invokes the Incident Management plan in case of a breach and uses an escalation process to be agreed to by both our clients and SM (sample below)
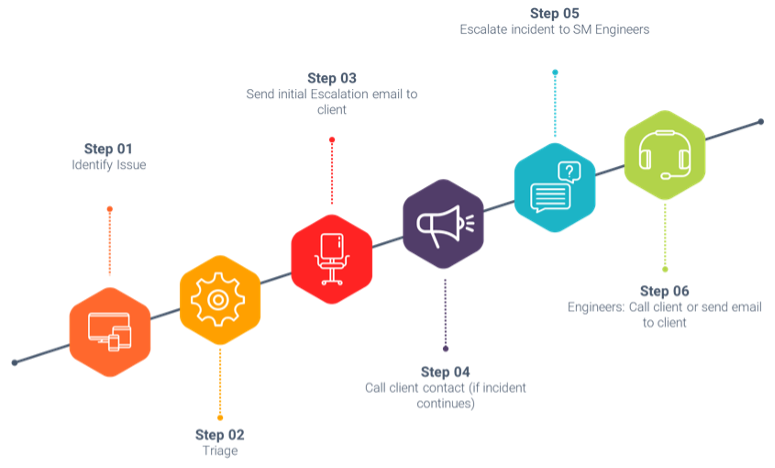
Our incident response services is based on NIST 800-61 framework and we have developed detailed steps to assist our clients during an incident. The SM framework is a single slide “table mat” with every phase and step listed:




 LevelBlue Features: Security Orchestration, Automation and Response
LevelBlue Features: Security Orchestration, Automation and Response









 Securely Managed SOC Services
Securely Managed SOC Services


