Similarly, the web application scanning feature of Frontline provides the highest level of dynamic web application testing results.
Patch Management
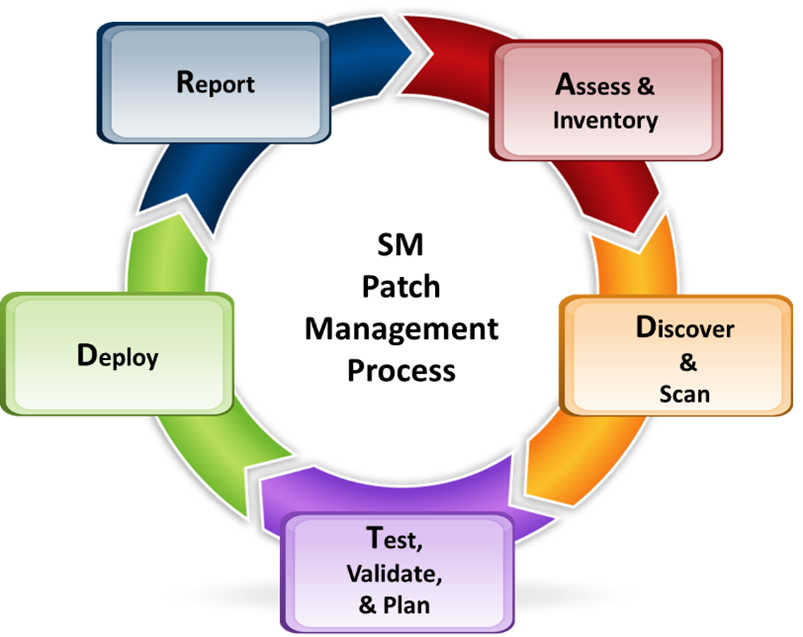
Our patch management methodology utilizes the following five steps and we can help organizations deploy a robust patch management program for you:
- Assess & Inventory: Using our client’s existing tools and procedures, we will review how the inventory is maintained of all assets with an IP address as well as the operating system and applications running on the asset.
- Discover & Scan: This area verifies the procedures on how our client discovers and scans new assets as well as perform scans to identify the missing patches. This step could also incorporate the vulnerability management process. For discovered devices, it is verified that it has current patches installed.
- Test, Validate, & Plan: In this area, we verify that a testing, validating and planning procedures are in place before the patch-updated systems are put in production. This is an important area to ensure the proper testing is performed before patches are rolled out to similar endpoints. A sample review will be performed for different types of endpoints.
- Deploy: In this area, we review how the patches are deployed to all the vulnerable systems and how the process incorporates the change management procedures. This assessment includes the automatic deployment of patches as well as the manual deployment. The review is also performed of the rollback procedure, in case the deployed patch has an issue.
- Report: In this area, we review all the communication which takes place amongst various UC stakeholders.