
One of the key components of Managed Detection Response (MDR) services to ensure comprehensive protection against advanced AI-enabled cyberattacks is the Identity Threat Detection and Response (ITDR).
What are Identity Threats?
Identity threats are those threats that target user accounts, credentials, and other identity related vulnerabilities. The hackers exploit these threats by using cyberattacks to gain unauthorized access to systems and data. These cyberattacks are techniques like phishing, credential stuffing, and password spraying to steal or misuse identities for malicious purposes, like performing lateral movement or escalating privileges within a network.
Identity-based attacks are currently the most focused and prevalent type of attack by hackers. They have surpassed previous top threats like software vulnerabilities and are now the primary attack surface, accounting for a majority of incidents, driven by the accessibility of tools like phishing-as-a-service platforms and infostealer malware. Other reasons why hackers focus on identity theft are:
- It is now easier for attackers to “log in” to systems using stolen or compromised credentials rather than trying to “hack” in through vulnerabilities.
- Identity compromise is the entry point for many other types of attacks, including malware, ransomware, and advanced persistent threats (APTs)
- The widespread use of stolen credentials from data breaches combined with sophisticated tools like credential stuffing and password spraying allows attackers to launch massive, automated attacks.
- Affordable tools like phishing-as-a-service platforms has lowered the technical bar for attackers.
- Identity-based attacks, such as business email compromise (BEC) and corporate account takeover (CATO), can lead to immediate and significant financial losses and operational disruption.
Common Identity-based Attack Methods
Here are some of the common identity-based attack methods used by cyber criminals:
- Phishing and social engineering: Deceptive emails or messages that trick users into revealing their credentials.
- Credential stuffing: Using large lists of stolen username and password combinations to log into multiple websites.
- Password spraying: Trying a few common passwords against many different accounts, rather than many passwords against one account, to avoid account lockouts.
- Infostealer malware: Malicious software designed to harvest credentials and other sensitive information from a user’s computer.
- Deepfake impersonation: Using AI-generated content to impersonate individuals for fraudulent purposes.
What are the criminals End Goal?
Although quite a bit of focus is on Business Email Compromise or BEC, the cyber criminals are usually not after email data, but the information stored on SharePoint.
SharePoint is often the main prize for attackers. It’s where companies keep the good stuff—sensitive docs, spreadsheets, contracts, credentials—all neatly organized and easy to search.
There are instances where attackers don’t even touch the mailbox. They log in, skip email entirely, and head straight for SharePoint.
And when they do, they move fast. Attackers can get their hands on sensitive data in less than 10 seconds.
It’s also worth remembering: SharePoint isn’t just a target – it can become a weapon. SM team has noticed that attackers use compromised SharePoint infrastructure to host malicious files and launch new phishing campaigns.
So next time you’re responding to a BEC, and all the focus is on login anomalies or inbox rules, stop and ask: What did the attacker get from SharePoint?
If SharePoint’s in scope for the attacker, it better be in scope for you as a defender too.
How can companies protect against Identity Threats?
Companies should think about layered cybersecurity protection and utilize Identity Threat Detection and Response (ITDR) systems. ITDR is a cybersecurity approach focused on finding and stopping threats that target user accounts, credentials, and other identity-based vulnerabilities. It involves monitoring user activity and identity systems for signs of compromise, such as leaked passwords or unusual login patterns, and then responding to mitigate the risks. This helps protect organizations from identity-based attacks like phishing and ransomware by strengthening their security posture around identities, which are becoming a new perimeter for security.
How Does ITDR work?
ITDR Focuses on:
- Detection: Continuously monitors risks like compromised credentials, risky user behavior, and identity system misconfigurations.
- Threat intelligence: Leverages information from sources like the dark web to identify stolen or leaked credentials.
- Response: Provides automated or manual responses to stop threats, such as locking compromised accounts or blocking malicious activity.
- Proactive posture: It also helps reduce the overall attack surface by identifying gaps in protection and securing privileged identities.
What is Enhanced ITDR?
Traditional ITDR tools were designed for an era with a clear perimeter and focused primarily on reactive alerts from identity systems. Enhanced ITDR moves beyond this by addressing the complexity of modern, decentralized cloud environments, where threats can emerge from various SaaS applications that often lack formal oversight. It focuses on preventing identity-based threats in modern SaaS environments, not just detecting and responding to them after they occur. This updated approach emphasizes continuous risk reduction by proactively identifying issues like unused credentials, excessive permissions, and risky integrations, and providing tools for immediate action to strengthen security posture.
What Can You Do?
Consider the following features of Enhanced ITDR when selecting a solution:
- Proactive prevention: It identifies and helps fix risks like stale accounts, weak passwords, and over-privileged users before they can be exploited.
- Comprehensive visibility: It provides visibility across the entire SaaS attack surface, including both managed and unmanaged applications.
- Real-time detection: It detects threats in real time, such as malicious OAuth grants or browser extensions, and correlates alerts with other security data for better context.
- Streamlined response: It enables quick-threat neutralization through one-click actions or automated workflows, reducing the time security teams spend on manual remediation.
- Posture improvement: It helps strengthen an organization’s overall identity security posture by providing guidance to fix identified gaps.
Integrating ITDR with MDR
To integrate ITDR with your Managed Detection and Response (MDR) solution, you can use native integrations within your selected ITDR solution (like Petra Security) where identity-based threat alerts are automatically escalated to the MDR team for investigation and response.
For multi-vendor environments, configure the ITDR solution to send security events to your Security Information Event Management (SIEM) platform where the MDR service is already monitoring, enabling the MDR team to correlate identity threats with other security data.
Majority of the time, SIEM software is used as a central hub. The ITDR solution can be configured to send security alerts directly to the SIEM. Ensure the MDR service is already ingesting and monitoring data from this SIEM. This allows the MDR team to correlate identity threat data with other logs (from endpoints, network devices, etc.) for a comprehensive view.
Create alert escalation and response playbooks and clearly define what constitutes a critical identity threat that should be escalated to the MDR team. Work with your MDR provider to develop specific response playbooks for identity-based threats (e.g., account lockout, password reset, session termination). The ITDR tool can automate initial containment actions, with the MDR team handling complex investigations and out-of-band responses.
In addition, continuously review the integration and the types of alerts being generated. Tune your ITDR rules and MDR playbooks to reduce false positives and ensure that genuine threats are being detected and responded to efficiently.
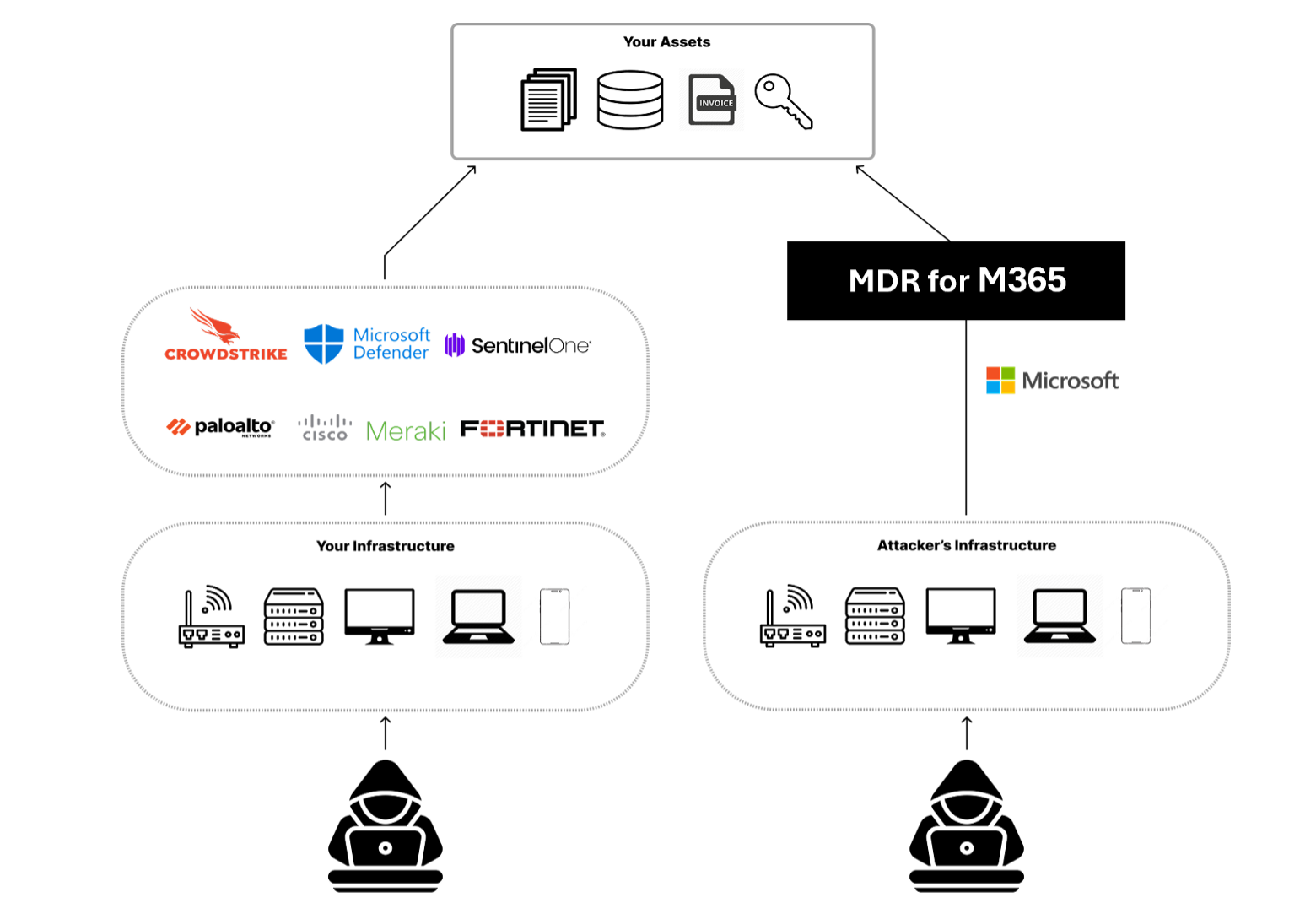
Petra Security
SM has partnered with Petra Security to provide you with the ability to monitor identity threats and integrate Enhanced ITDR capabilities with the SIEM and SOC. Petra detects attackers in your M365 environment, kicks them out, and gives you a detailed report of everything they did. Petra gives you a fast and easy way to search for all your M365 logs. Whereas SIEM generally tells you, “Jack clicked on an email in his Inbox at 9:04 am.”, Petra will tell you the title of the email, senders and recipients, whether it has attachments, etc.
In addition, Petra:
- Catches attacks Microsoft licensing layer of P2 misses. P2 only looks at logins. Petra looks across logins and activity like which emails a user is reading / sending, which SharePoint docs they’re accessing, what Teams messages they’re reacting to etc. Petra catches attackers that don’t show up in logins
- Less noise. Because it can analyze across all these streams, it can correctly dismiss false positives, like when an employee is traveling. When Petra notifies you, it’s almost always an attack.
- Traces user activity across Entra ID, Outlook, SharePoint, Teams and more. SIEM can do detections on each of these individually, but not across them.
- Petra is purpose-built for M365, so it processes every bit of activity. For example, in addition to what SIEM can ingest, Petra monitors app registrations, devices registrations, authentication method changes, user permissions changes, and email metadata.
Petra integrates seamlessly to protect your M365 environment in the cloud like your other security products protect your on-prem environment:
Enhanced ITDR Managed Security Services are available from SM. Please contact us at info@securelymanaged.com for more information or to set up a demo of Enhanced ITDR solution.