Comprehensive Managed Detection and Response (MDR) Services
Securely Managed provides comprehensive Managed Detection and Response services to our clients as shown in the diagram below:
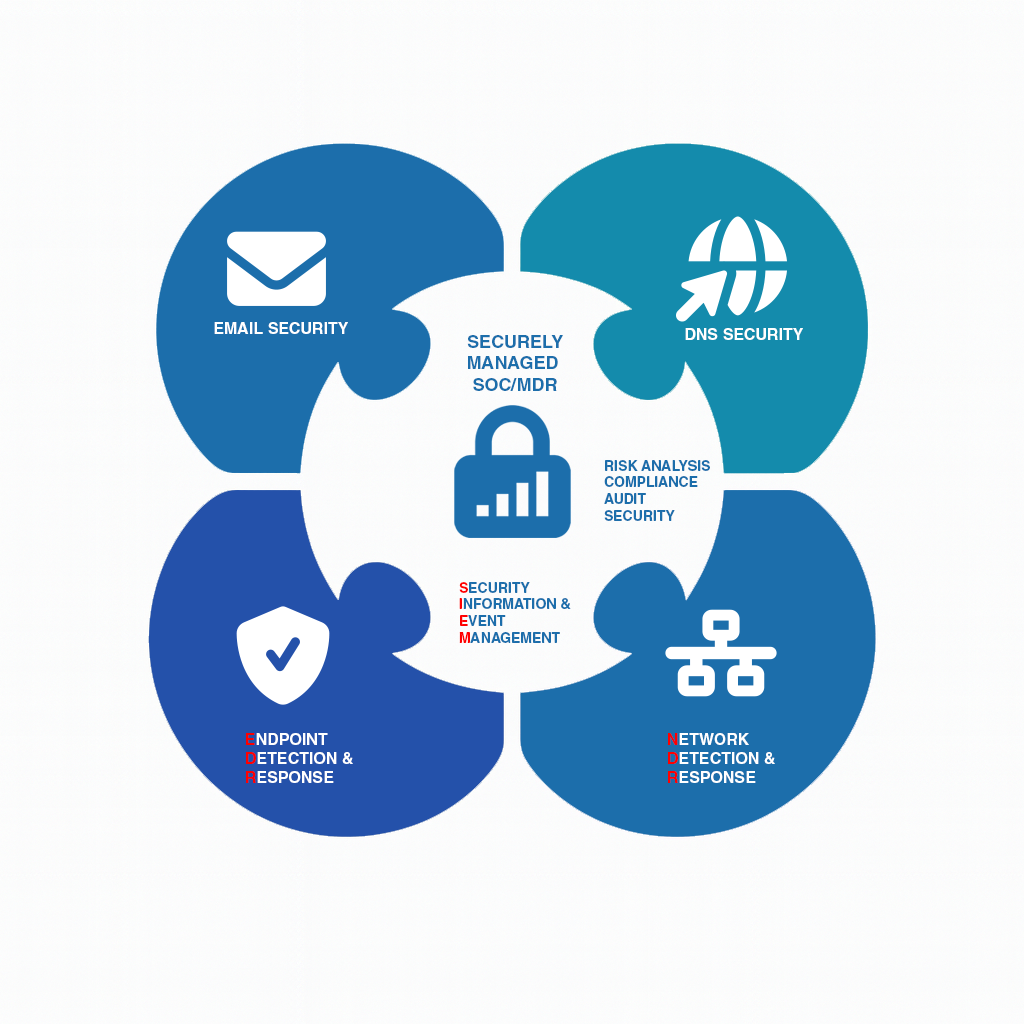
The foundation of these services consists of two components:
- Security Information and Event Management (SIEM) platform which enables organizations to have a single pane of glass to detect and monitor the activities within their environment.
- Security Operations Center (SOC) combining expert analysts with advanced technology (AI, machine learning) for 24/7 monitoring, proactive threat hunting, rapid detection, investigation, and response to cyber threats, protecting endpoints, networks, and cloud environments to fill security gaps and reduce breach impact for organizations. It goes beyond simple alerts, offering continuous security operations to stop sophisticated attacks like ransomware, ensuring rapid containment and recovery without requiring massive internal staff.
SM has partnered with LevelBlue and provide USM Anywhere as the SIEM solution (previously called AlienVault). SM has been providing SOC services since 2017, and its entire SOC is located within USA.
By combining the SIEM and the SOC components, SM is in a position to provide premier Managed Detection and Response (MDR) services. Our MDR services consists of:
- 24/7 Monitoring & Detection: Continuous surveillance of your entire digital environment (endpoints, cloud, network) for suspicious activity.
- Human Expertise: Access to a remote Security Operations Center (SOC) with skilled analysts who investigate alerts, hunt for hidden threats, and handle complex incidents.
- Advanced Technology: Utilizes AI, machine learning, and threat intelligence to filter noise and identify advanced threats.
- Proactive Threat Hunting: Actively searching for unknown threats that bypass automated defenses, rather than just waiting for alerts.
- Rapid Incident Response: Swift containment and remediation of identified threats, often with pre-approved actions, minimizing damage.
- Threat Intelligence: Leveraging global and customized intelligence to understand and predict attacker behavior.
Our MDR services provide several benefits:
- Fills Skills Gap: Provides elite security expertise without hiring more staff.
- Reduces Time-to-Detect: Cuts detection time from months to minutes, drastically limiting attack impact.
- Proactive Security: Shifts from reactive to proactive defense against advanced threats.
- Cost-Effective: Offers 24/7 SOC capabilities at a fraction of the cost of building one in-house.
- Improved Security Posture: Boosts overall security resilience and brand reputation.
Other MDR Components
Deployment of Honeypot
SM highly recommends the deployment of Honeypot on the network. Honeypot is a decoy computer system, application, or data set designed to attract and trap cyber attackers, luring them away from real assets to study their methods, tools, and behaviors for defensive purposes, acting as a digital trap to gather threat intelligence and improve security. These fake targets mimic valuable systems, but any interaction with them provides valuable insights into malicious activities, from simple probes to complex attacks, without risking actual data.
SM’s SOC continuously monitors the Honeypot activity. In a normal environment, there should be no or minimal activity in the Honeypot. In case there is abnormal increased activity, it is monitored by SOC and analyzed for any malicious attacks on the network.
SM is currently providing free deployment and monitoring of Honeypot to our existing clients.
Endpoint Detection and Response (EDR)
Most organizations have EDR software installed on their endpoints, whether it is Microsoft Defender, CrowdStrike, SentinelOne or one of the other common EDR software. EDR software plays a key role as a first line of defense against malware and other attacks on endpoints. EDR software should integrate with SIEM and can provide automation through Security Orchestration and Automation Response (SOAR) features of EDR and SIEM.
SM’s SOC can integrate the logs from EDR and can automate SOAR functions via SIEM. If your organization is looking for an EDR solution, SM can provide you with a solution from CrowdStrike or SentinelOne.
SM’s USM Anywhere SIEM integrates seamlessly with CrowdStrike, SentinelOne, Microsoft Defender and other leading EDR software.
Network Detection and Response (NDR)
Network Detection and Response (NDR) watches network traffic for threats, while EDR monitors individual devices (endpoints); they complement each other, with NDR catching lateral movement and network-based attacks, and EDR stopping malware and suspicious activity on a specific computer, making them both crucial for comprehensive security, as one offers a “bird’s-eye” view and the other a “boots-on-the-ground” perspective.
According to Gartner, NDR+EDR+SIEM is a strategic approach to achieve comprehensive threat visibility across an organization’s digital landscape. Gartner also says that organizations that integrate NDR, EDR and SIEM solutions have reported a 50% faster response to cyber incidents.
SM has partnered with Vectra AI to provide AI enabled NDR solution, which integrates with USM Anywhere SIEM and can be monitored through SM’s 24x7x365 SOC.
Identity Threat Detection and Response (ITDR)
Identity-based attacks are currently the most focused and prevalent type of attack by hackers. They have surpassed previous top threats like software vulnerabilities and are now the primary attack surface, accounting for a majority of incidents, driven by the accessibility of tools like phishing-as-a-service platforms and infostealer malware. Other reasons why hackers focus on identity theft are:
- It is now easier for attackers to “log in” to systems using stolen or compromised credentials rather than trying to “hack” in through vulnerabilities.
- Identity compromise is the entry point for many other types of attacks, including malware, ransomware, and advanced persistent threats (APTs)
- The widespread use of stolen credentials from data breaches combined with sophisticated tools like credential stuffing and password spraying allows attackers to launch massive, automated attacks.
- Affordable tools like phishing-as-a-service platforms has lowered the technical bar for attackers.
- Identity-based attacks, such as business email compromise (BEC) and corporate account takeover (CATO), can lead to immediate and significant financial losses and operational disruption.
- Major tools and solutions vendors are quick to patch vulnerabilities in their solutions and as such making it harder for hackers to target only tools.
- While many organizations perform security awareness trainings and tests, companies still do not achieve 100% success rate. Hackers attack this human loophole to gain access to the organization’s data.
- For many organizations, security is still an afterthought. Only after an incident has occurred does management devote appropriate effort to security.
- Organizations forget the inter-connection of many organizations. A small company may provide services to a large organization and may have access to the large organization’s network. The hacker is initially interested in the small company so that the hacker may harvest credentials to use in attacking the large organization.
SM has partnered with Petra Security to provide you with the ability to monitor identity threats and integrate with the SIEM and SOC. Petra detects attackers in your M365 environment, kicks them out, and gives you a detailed report of everything they did. Petra gives you a fast and easy way to search for all your M365 logs. Whereas SIEM generally tells you, “Jack clicked on an email in his Inbox at 9:04 am.”, Petra will tell you the title of the email, senders and recipients, whether it has attachments, etc.
In addition, Petra:
- Catches attacks Microsoft licensing layer of P2 misses. P2 only looks at logins. Petra looks across logins and activity like which emails a user is reading / sending, which SharePoint docs they’re accessing, what Teams messages they’re reacting to etc. Petra catches attackers that don’t show up in just logins
- Less noise. Because it can analyze across all these streams, it can correctly dismiss false positives, like when an employee is traveling. When Petra notifies you, it’s almost always an attack.
- Traces user activity across Entra ID, Outlook, SharePoint, Teams and more. SIEM can do detections on each of these individually, but not across them.
- Petra is purpose-built for M365, so it processes every bit of activity. For example, in addition to what SIEM can ingest, Petra monitors app registrations, devices registrations, authentication method changes, user permissions changes, and email metadata.
ITDR Managed Security Services are available from SM’s 24x7x365 SOC.
DNS Detection and Response
Every time your employees go online—loading websites, using cloud apps, or syncing data—your systems rely on the Domain Name System (DNS) to get them where they need to go. DNS quietly translates domain names into IP addresses, making everything happen behind the scenes.
But DNS isn’t just for the good guys. Attackers and intruders rely on it, too—to communicate with malware, steal data, and disguise malicious activity. For any organization, especially smaller ones, this creates a significant risk: the same system that keeps you running can also expose you to threats if left unprotected.
SM offers affordable DNS security as part of our MDR services, monitor and control DNS traffic so you can stop attacks before they cause damage.
SM has partnered with leading DNS software provider, Infoblox to provide DNS Detection and Response Services through our 24x7x365 SOC. SM also provides a free DNS assessment.
For more information on SM’s comprehensive MDR services, please visit our Website, www.securelymanaged.com.