
SM highly recommends the deployment of Honeypot on the network. Honeypot is a decoy computer system, application, or data set designed to attract and trap cyber attackers, luring them away from real assets to study their methods, tools, and behaviors for defensive purposes, acting as a digital trap to gather threat intelligence and improve security. These fake targets mimic valuable systems, but any interaction with them provides valuable insights into malicious activities, from simple probes to complex attacks, without risking actual data.
SM’s SOC continuously monitors the Honeypot activity. In a normal environment, there should be no or minimal activity in the Honeypot. In case there is abnormal increased activity, it is monitored by SOC and analyzed for any malicious attacks on the network.
Honeypot Deployment
A honeypot deployment strategy involves placing decoy systems (honeypots) in a network to lure attackers, gather intelligence on their methods, and distract them from real assets, using tactics like virtual machines, honey tokens, or honeynets for internal threat detection (insider threats) or external research, with key steps including defining objectives, isolating the honeypot, making it believable, and continuous monitoring for actionable threat insights.
Key Components of the Strategy
SM SOC team recommends considering the following strategy components when designing the deployment of a Honeypot:
- Define Objectives: Determine goals, such as detecting automated scans, analyzing advanced persistent threats (APTs), or stopping insider threats.
- Choose Honeypot Type:
- Low-Interaction: Simulates basic services (e.g., open ports) for broad threat collection, easier to manage.
- High-Interaction: Emulates full operating systems for deep analysis of attacker behavior, higher risk/reward.
- Honey Tokens: Fake credentials or data (e.g., database entries) placed in real systems to trigger immediate alerts when accessed.
- Decide on Deployment Location:
- External/Internet-Facing: Gathers broad attack data but creates noise.
- Internal: Detects lateral movement and insider threats within the network.
- Isolation: Crucial step to segment the honeypot from the production network using VLANs or subnets to prevent compromise of real assets.
- Believability: Configure hostname, services, and OS to match the production environment to avoid detection.
- Monitoring & Logging: Implement continuous monitoring and real-time alerts to capture all attacker actions (commands, traffic) and store logs securely.
- Analysis & Response: Use collected data (IPs, attack patterns) to understand threats, improve defenses, and create real-time alerts for security teams.
Example Strategies
- Sacrificial Lamb: Intentionally exposing a vulnerable server to attract attackers, providing time to study their methods.
- Decoy Asset Injection: Placing fake databases or cloud accounts within a live network to catch credential thieves.
- HoneyNet: A network of interconnected honeypots to map complex attacks.
The following diagram shows a typical deployment of Honeypot:
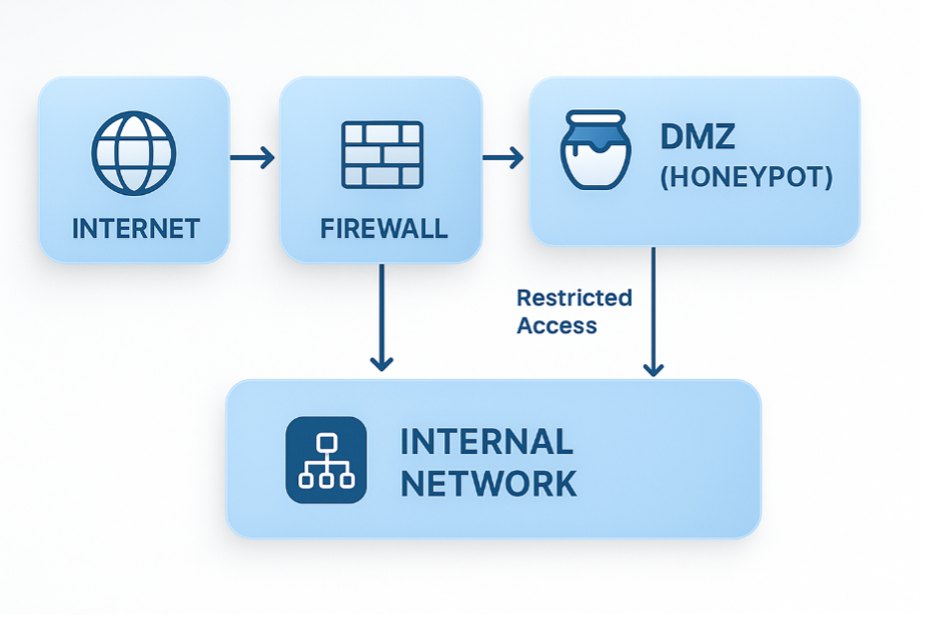
SM and T-Pot
SM and its SOC team can help discuss the deployment strategies. SM utilizes an open-source Honeypot called T-Pot. T-Pot honeypot is deployed by setting up a Linux virtual machine (VM) in the cloud (like Azure) or locally, installing Docker, then cloning the T-Pot repository and running its installer script, which sets up multiple honeypots (like Cowrie, Dionaea) and a web interface (ELK Stack) for monitoring attacks, requiring an initial VM setup, SSH connection, and configuration via prompts to choose deployment types (like Hive) and credentials, with a reboot to finalize.
Honeypot Benefits
SM SOC team has seen the following benefits for those clients who have implemented the Honeypot:
- Detect malicious behavior early
- Analyze attacker TTPs (tactics, techniques, and procedures)
- Collect real-world malware samples
- Learn how adversaries move
- Generate threat intel for your SOC/MSSP
SM is currently providing free deployment and monitoring of Honeypot to our existing clients.
For more information on SM’s comprehensive MDR services, please visit our Website, www.securelymanaged.com.